
Hackers Can Exploit Pre-Installed Samsung Apps to Spy On Users
Hackers can spy on Samsung users. The problem was reported to Samsung’s bug bounty program
Press esc. or click anywhere outside to close the search bar.

Hackers can spy on Samsung users. The problem was reported to Samsung’s bug bounty program

Researchers have discovered serious flaws in Realtek Wi-Fi modules that a criminal could exploit to

On Tuesday, 1st June 2021, the hackers attacked JBS, the largest meat processing company in

Stolen API Keys are one of the leading causes of huge financial losses in cryptocurrencies.

Experienced cybersecurity professionals use penetration testing to strengthen a company’s security posture and eliminate flaws

As cyberattacks are becoming the norm now, it is more important than ever to conduct

A chain is as strong as its weakest link, and that’s why even if a

To help protect from this, we may have multiple layers of protection in our system.
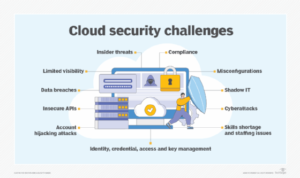
Cloud computing has provided businesses with the option to scale up the organization and introduce

Most Popular Phishing Attacks & How a Cyber Security Company Can Help You
At Rogue Logics, we know that advanced cybersecurity and AI solutions require a tailored approach. Whether you’re a growing startup or a global enterprise, we customize our services to align perfectly with your unique business needs.