Zero Day Attacks – Understanding how it works and Prevention Tips

To help protect from this, we may have multiple layers of protection in our system. This includes firewalls, scanners, encryption, next-gen security protocols, and all the other fancy names. Sure, these protection systems work and keep us away from everyday problems, however, these devices can still miss an Attack.
5 Common Cloud Security Threats and How to Mitigate Them
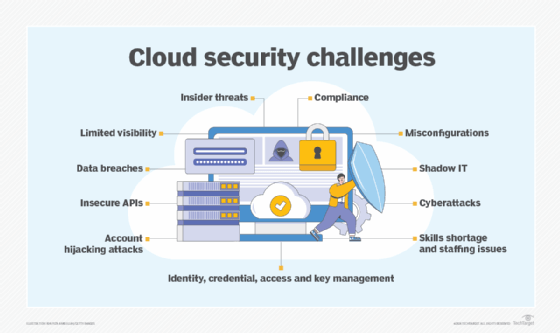
Cloud computing has provided businesses with the option to scale up the organization and introduce flexibility. But at the same time, it has exposed networks to increased data breaches and attacks. The attack on the network can result in a potential loss of information, time, and money. Hence, prevention is always better in this case.
Phishing Attacks – How to Prevent Them?

Most Popular Phishing Attacks & How a Cyber Security Company Can Help You
