Warning!!! Malicious Content Is Served Via Archive.Org

Professionals have recently found malevolent and violating content on Archive.org. Malicious content can be anywhere, but you just need to use the internet vigilantly to secure your data.
Incident Response And How To Best Handle It

do you know a well-defined incident response plan (IRP) enables you to identify, mitigate the damage, and lower the cost of a cyber assault!
A Colossal Cyberattack Hit 200 Businesses Around the World…

On July 3rd, 2021, a cyberattack resulted in the closure of 200 businesses around the world. This attack directly or indirectly affected the businesses involved in the supply chain.
Cobalt Strike Has Become One of the Hacker’s Favorite Tool

Cobalt strike has become one of the Hacker’s Favorite Tool. It has now become one of the most abused tools in the world of cybercrime.
Apple’s macOS and iOS Aren’t Fully Safe as You Might Think…

Apple and Security are known to be synonymous but is it really the case?
Smart Building and the Need for Cybersecurity

Smart technology is everywhere, literally, from your phone to your laptop, to your doorbells and CCTVs. These technologies have made their way deep into our lives. We spend more time staying online and connected than ever, and with the advent of COVID, our lives have depended on the internet and smart technologies more than ever. […]
Ransomware Attack on Meat Processing Plants of JBS

On Tuesday, 1st June 2021, the hackers attacked JBS, the largest meat processing company in the world. This attack has raised many questions on the need for and importance of cybersecurity issues prevailing in the industry and how these cybersecurity attacks lead to national security issues. What happened in the JBS meat processing hack? JBS […]
Zero Day Attacks – Understanding how it works and Prevention Tips

To help protect from this, we may have multiple layers of protection in our system. This includes firewalls, scanners, encryption, next-gen security protocols, and all the other fancy names. Sure, these protection systems work and keep us away from everyday problems, however, these devices can still miss an Attack.
5 Common Cloud Security Threats and How to Mitigate Them
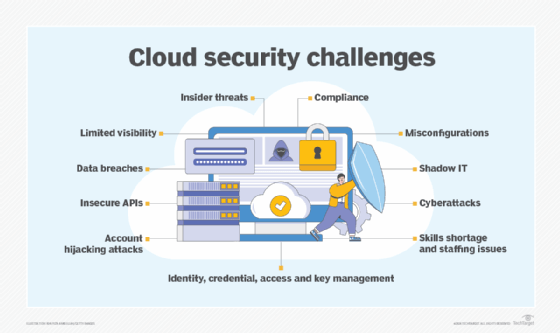
Cloud computing has provided businesses with the option to scale up the organization and introduce flexibility. But at the same time, it has exposed networks to increased data breaches and attacks. The attack on the network can result in a potential loss of information, time, and money. Hence, prevention is always better in this case.
Phishing Attacks – How to Prevent Them?

Most Popular Phishing Attacks & How a Cyber Security Company Can Help You
